Schrift Encryption - is a European patent-protected end-to-end encryption (or E2EE) solution. Officially published in the European Patent Bulletin of 12.03.2025 (page 1170).
Official certificate of European patent.pdf
For any cloud service, it is extremely important to ensure the security of customer data. And it is certainly beneficial for a client to have confidence that only they have access to their data and no one else. But it's even better to not just trust the cloud service's assurances, but to understand how its data is handled.
This is especially important when client data is not just a file sharing folder, but a key component of the information system, a platform for internal and external communication, storage of confidential documents and corporate knowledge base, i.e. a place of concentration of confidential information of the organisation or a personal data safe of an individual user.
When a cloud service declares data encryption, it usually only refers to the data transfer between the cloud server and the client. But encryption of this traffic is already a standard feature of all Internet browsers. Otherwise, the user receives a serious warning from the web browser about the danger of continuing to work.
Customers are usually unaware of how their data is stored and processed on the cloud service servers. There are frequent media reports about data leaks from cloud services as a result of hacker attacks or negligence of service providers or data centres.
A customer's own server is no better in terms of data security, as all the risks of a cloud server are equally or even more relevant to a local server.
We don't just declare that we don't have access to customer data when Schrift Encryption is activated, but also confirm this with a detailed description of the technology, because we respect our customers and know how important and useful this service is to them.
How Schrift Encryption works
Client data in decrypted form can only be stored on client devices. The data created by the client is encrypted on the user's device and transmitted to our server (cloud service) in an encrypted form.
Client data never goes online or appears on our servers in decrypted form, even in transit, even for a short period of time. We do not have access to client data, and neither do any intruders who may potentially access our servers.
All data encryption and decryption operations take place on the user's device, locally, not on our server, so no one but the client can access the decrypted data. Neither our employees (cloud service administrators), nor data centre administrators, nor hackers, nor law enforcement agencies, with or without court orders, can access customer data without the customer's consent. We, as the cloud service provider, will not be able to disclose the client's information, either voluntarily or under pressure, because we do not have such technical capabilities.
Schrift performs its functions by working with encrypted data, using only digital identifiers of documents, events, files, etc. that are of no use to unauthorised persons without access to the semantic information.
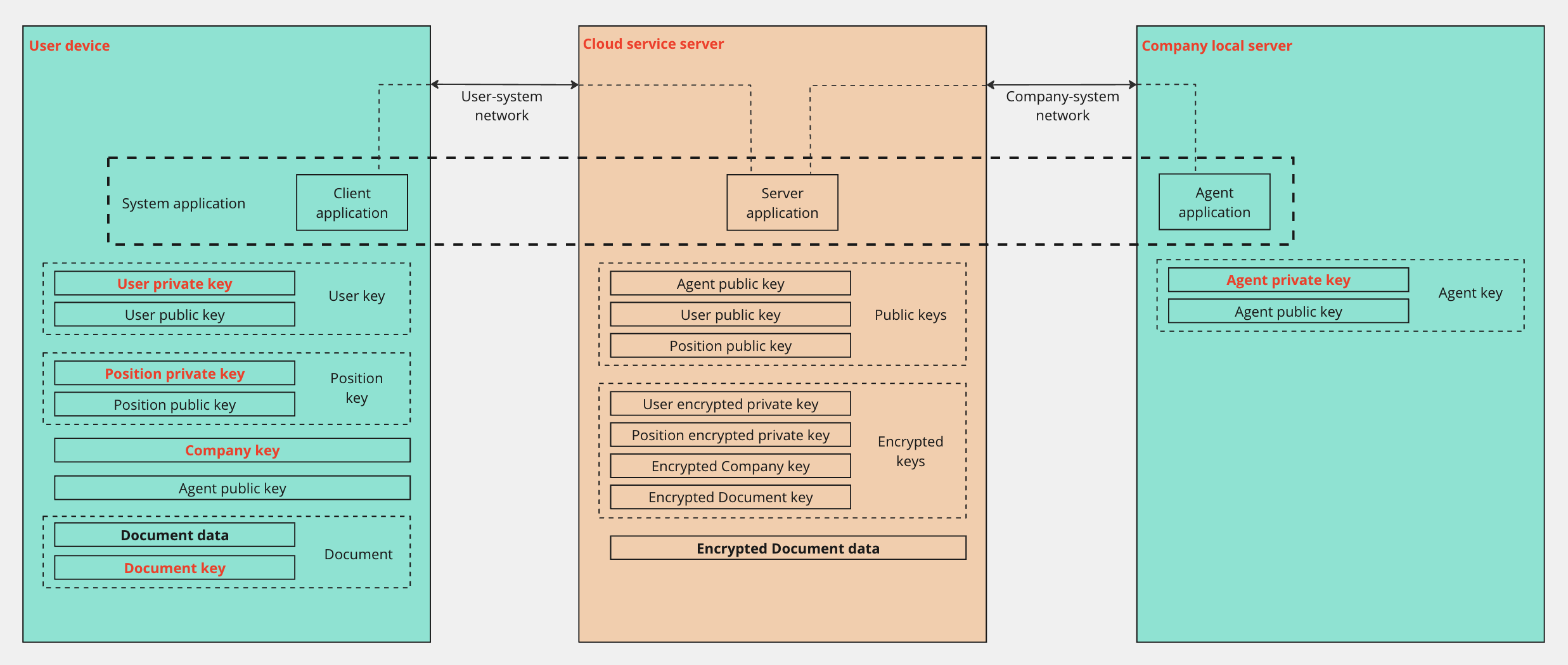
One of the key components of encryption technology is the encryption agent. This is a separate application that is deployed in a docker container and installed by the client independently in their infrastructure (on a server or on a regular computer). Only the client has access to the encryption agent. Below are the main operations of the Schrift Encryption technology:
-
When activating company encryption, the company administrator creates a pair of agent keys: public and private, as well as a company key (symmetric). The company key is used to encrypt company directories: employees, positions, counterparties, document templates, document types, etc.
-
When a user accesses the data of an encrypted company on their device, they automatically create a pair of encryption keys: a public key (used to encrypt the data) and a private key (used to decrypt the data). The private key is available only to the user, and the public key is transferred to the server for use by the encryption agent.
-
The encryption agent performs the function of creating a pair of keys for a new position: private and public. When the administrator or another employee of the company creates an employee assignment to a position, the encryption agent encrypts the private key of the position with the user's public key and transmits it to the server for transmission to the assigned employee.
-
During the authorisation process, the user receives the encrypted private key of the position and the company key from the server, decrypts them with the user's private key, and is able to work with the data available to his position.
-
When creating a new document (task, folder, chat, etc.), the employee creates a document encryption key (symmetric), encrypts the document data with this key, encrypts the document key with the public key of the position and the public keys of the encryption agent and each of the positions to which he/she grants access to this document, transfers the encrypted document and the encrypted document key to the cloud server.
-
When accessing the document, the employee receives the encrypted document and the encrypted document key from the cloud service, decrypts the document key with the private key of his or her position, and decrypts the document with the document key.
-
The encryption agent ensures that the position has access to all documents registered in the registration log to which the position has been granted the right to read. To do this, the encryption agent receives from the server the document keys encrypted with the agent's public key, decrypts them, and transmits the document keys encrypted with the public key to the server to the position that needs to be granted access to such documents.
-
The encryption agent performs operations to create pdf previews and graphical thumbnails of files necessary for the convenience of users working in the system. To do this, the encryption agent receives a file encrypted with the document key and the document key encrypted with the agent's public key from the server, decrypts the document key and the file, creates a pdf preview and thumbnail, encrypts them with the document key, and transmits them to the server. The system supports the creation of pdf previews and thumbnails for more than 100 file formats.
-
The encryption agent creates an index for full-text searching of documents, events, files, and file contents. To do this, the encryption agent receives data encrypted with the document key and the document key encrypted with the agent's public key from the server, decrypts the document key and data, creates a full-text index, and transmits it back to the server.
The function of the encryption agent is to constantly stay in touch with the cloud service, which cannot be required of the administrator or company owner. This allows the agent to perform scheduled tasks and resource-intensive operations.
For example, a company administrator adds a new employee, creates a position assignment for him or her, for example, from 9 am tomorrow morning. As a result, the new employee must receive the private key of the position, but not before the start of his or her appointment. However, it is not known when exactly the new employee will connect to the system, create his account, and generate his key pair. Therefore, the encryption agent, being constantly ready to do its job, will issue the new employee the position key at the appropriate time: no later than the user registers the account and no earlier than the start of the period of his or her appointment.
All agent operations are logged and these records can be checked by client administrators. The agent is limited in its ability to independently call data from the cloud provider's service to decrypt and read it. The agent performs its work only within the tasks it receives from the cloud provider's server.
If the encryption agent loses connection with the cloud service for some reason, the company's work will not stop. However, some operations will not be able to be performed until the agent comes back online. These include:
-
new appointments to positions;
-
opening access to a document, if the position has not yet had access to this document, and the opening of access follows from the process of automatically sending a document for signature;
-
create previews and thumbnails for files;
-
update the full-text search index.
When the encryption agent comes back online, all pending tasks will be immediately completed by it.
Technology productivity
In addition to the exceptional level of security of the technology, its special value lies in its reliability and maximum performance when working in a multi-user environment.
This is ensured by the fact that the 3 main levels of keys (user, position, document) provide the fastest possible result in the following practical examples:
-
When a user changes his password, his key pair changes. The encryption agent provides the user with the private key of the position, which is encrypted with the user's new public key. This way, there is no need to re-encrypt documents and their access keys. Execution time: 1-2 seconds.
-
When a new position assignment is created, the encryption agent transmits the position's private key to the user, encrypted with the user's public key, and the employee (user) gains access to all data available to the position. Execution time: 1-2 seconds.
-
When an employee is terminated from a position, the position's private key encrypted with the user's public key is deleted from the server. Thus, the user's access to the position is terminated without the need to re-encrypt documents and access keys to them. Execution time: 1-2 seconds.
The processes of creating a new document and the key to encrypt it, as well as the processes of encrypting the document and decrypting the data, take time that is slightly different from the time required to work with unencrypted data. Usually, this is no more than 20-30 additional milliseconds.
Peculiarities of information transfer in external communications
If an encrypted company (K1) sends a document to an unencrypted company (K2), the document will be decrypted by an agent before being sent via the Schrift Intercompany service.
If an encrypted company (K1) sends a document to an encrypted company (K2), then before sending the document, the encryption agent K1 receives the public key of the encryption agent K2, encrypts the document key and transmits the document via the Schrift Intercompany service in encrypted form. Encryption Agent K2 decrypts the document key with its private key and distributes access to the document to the respective K2 positions.
Additional data protection factors
The technology eliminates the possibility of changing the agent's encryption keys when encryption is active in the company, i.e. the data is in an encrypted state. This means that no one, neither the server administrator nor an attacker, can change the agent's keys.
Even knowing the encryption keys of the agent does not give access to the data, as Schrift Encryption technology is a second, additional layer of information protection, in addition to the business logic of the Schrift DMS, which provides data access control.
The API key performs an additional function of data protection:
-
To run the encryption agent on another server, you need to know the API key. Without it, it is impossible to run the agent, even if you have the agent's encryption keys.
-
Only the company owner or administrator, if authorised, can obtain a valid API key. The API key can be obtained in the company account, in the Security tab.
-
When you receive a new API key, the previously created API key becomes invalid. Thus, if an encryption agent is authorised to the system and is running, and a new API key is created in the system, the encryption agent will lose access to the system until a new API key is entered in the encryption agent authorization web interface.
Technology vulnerabilities
The main vulnerability of end-to-end encryption (E2EE) lies not in the technology itself, but in the endpoints (devices used by end users). If an attacker gains access to the sender's or recipient's device, they can access the information being transmitted. This means that data security also depends on the security of the device and user account. Read more about user account security in the article.
It's important to note that these vulnerabilities are not specific to end-to-end encryption, but apply to any data scheme that has endpoints.
