Data security requirements are constantly increasing. The more data you have in your management system, the greater the return on investment, and the security of your system becomes a top priority. Sсhrift fully meets these challenges.
Our system guarantees a secure way to work with data, store it and communicate with partners, with a modern interface and easy-to-use functionality, and no matter where you are or what device you use.
The system protects customer data with all modern tools and virtually eliminates the risk of data loss or leakage due to ransomware and other hacker attacks.
Links to our certificates of compliance of our information security management system with ISO/IEC 27001:2022 issued by leading German certification bodies.
Sсhrift provides protection against XSS (Cross-Site Scripting) attacks. XSS is a common type of web attack that involves the injection of malicious code into a website or application page.
Schrift proxies all requests for links to external resources that are received in documents, emails and other system objects. This protects the IP address of the client's endpoint device on which it works in our system.
User account security
We pay special attention to the security of your account. Read more about this in the article.
Read about the logic of the Schrift system: “company - position - assignment - employee - user” in the article Administering a company.
Secure data storage and transmission
Data transmission. Client connections are encrypted using the HTTPS/TLS protocol (TLS 1.2 or higher), which means that all traffic between the client and us is protected during transmission.
Schrift automatically scans uploaded files for viruses. If a file is detected, it is blocked from downloading and is marked accordingly in the interface.
Data storage. The data on our servers is encrypted using AES-256 keys and is stored on secure servers located in Germany.
End-to-end data encryption (E2EE) technology provides the highest level of data security, when no one but the client (employees) can access the decrypted data. Read more in the article Schrift Encryption Technology.
Secure backup. To eliminate the risk of data loss, data is continuously backed up to several physically distributed servers.
The data of each company on our servers is isolated, which ensures protection at any time and prevents access to other users' data.
To further mitigate the risk of unauthorised access to company data at the employee level, the company can enable employee identification by QES/AES.
The advantage of a cloud service over an own server
Firstly, the company's data is reliably protected by a set of tools and methods used for our cloud server infrastructure.
Secondly, the most common cases of customer data breaches occur as a result of compromised system administrator accounts due to negligence or intent.
With the use of end-to-end data encryption, the risk of company data leakage is basically eliminated, because neither company administrators nor cloud server administrators have access to the data, and the encryption agent, although located in the client's infrastructure, has access only to the data for which it has received a request to process. Read more in the article Schrift Encryption Technology.
This means that there is no need to depend on whether the company employee responsible for administering servers with sensitive data will be responsible, attentive and loyal enough to the company's interest to give the company owner peace of mind about data security.
Administering access to data
The tools in the Company Settings section, such as the role system, communication rights for positions, including subordination rules, and other administration methods, provide flexible configuration and reliable protection of rights.
The role model contains the system roles of Owner, Administrator, User, etc. The Owner role has special protection against unauthorised removal. We support the creation of custom roles that can be assigned different permissions, providing granular access to certain rights.
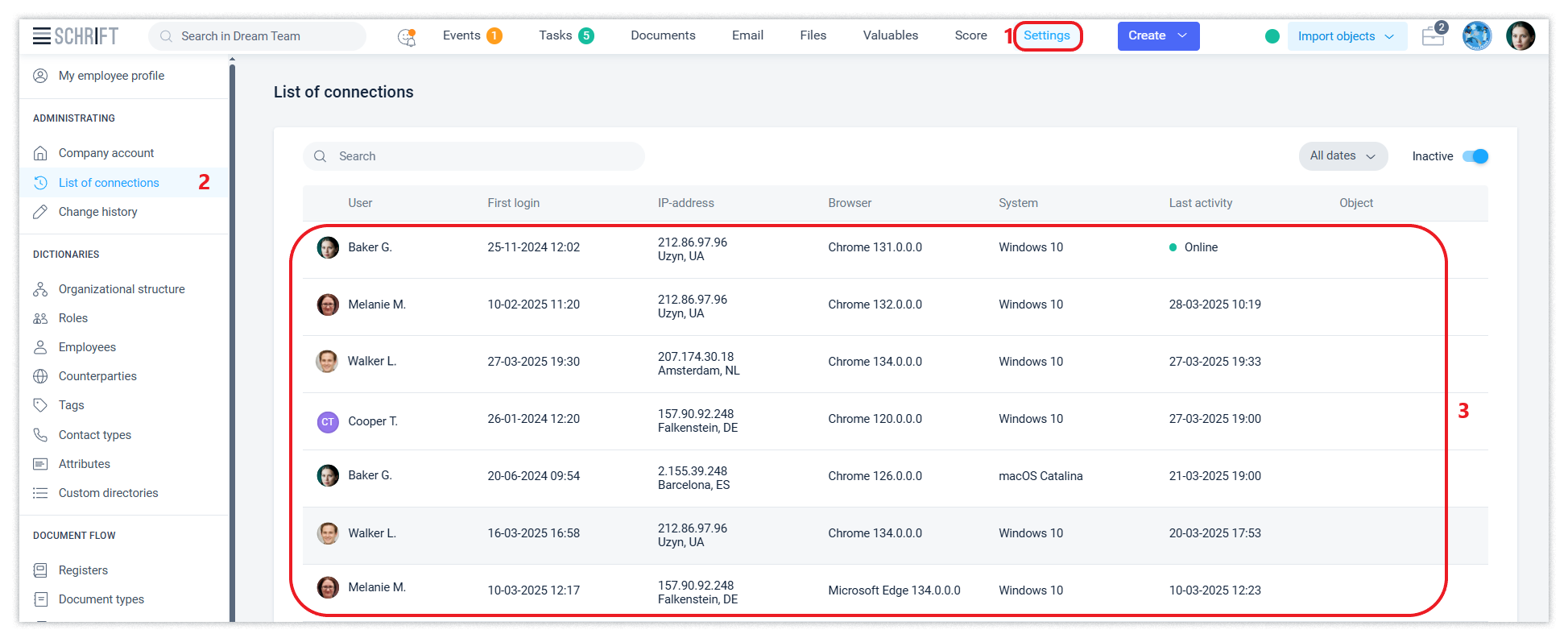
The company account contains a history of employee connections with information about the devices and locations from which connections were made, as well as a history of changes to all directories in the Settings section.
Flexible access settings by setting one of three levels of access to data (basic, confidential and secret) at the level of employee appointment and at the level of the system object makes it possible to protect confidential and secret documents, as well as restrict access to information of the available position by an assistant or acting.
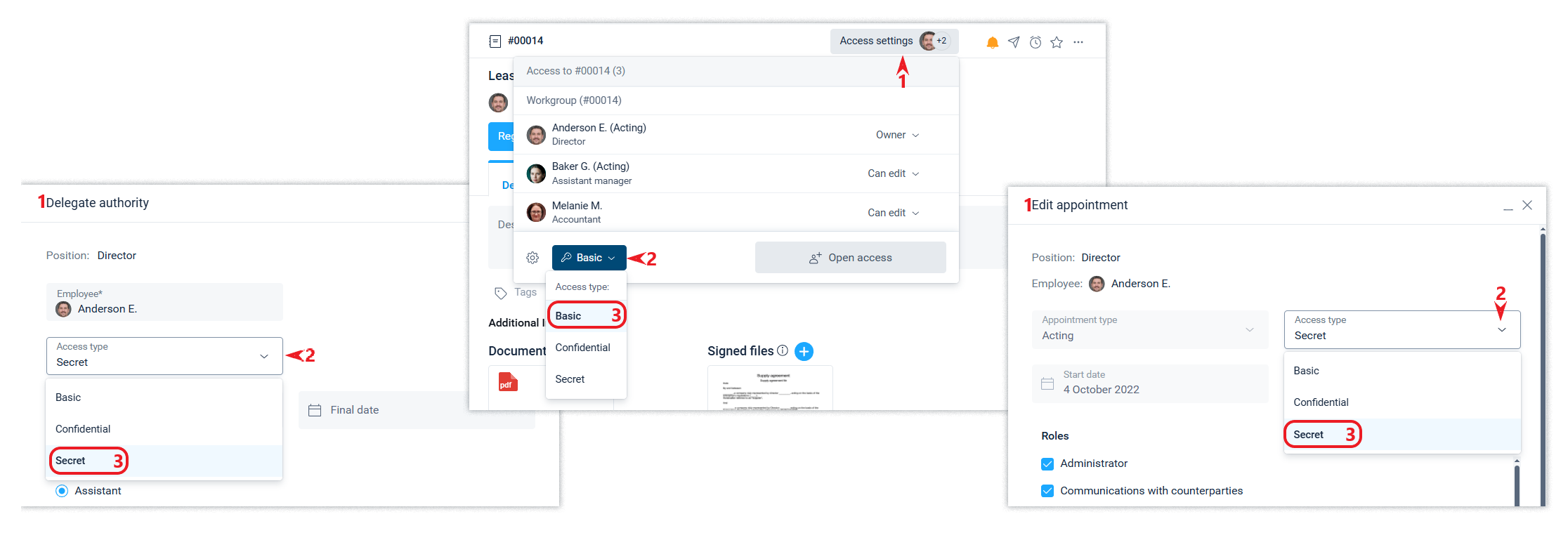
Access rights and protection against falsification. Access to the company's data is granted to an employee through appointment to a position. The user acquires the status of an employee in the company as a result of accepting the corresponding invitation to his/her email.
When a user clicks on a link from an invitation letter to join the company, a user-employee link is created. Once this connection has been established, no one can break it to give another user the right to act on behalf of the employee. This ensures that no one other than the employee can perform actions in the company on their behalf. Read more about this in the article.
An employee with privileged rights (owner, administrator, etc.) cannot grant himself access to another position (create an appointment) without the system automatically informing the employee who is regulary appointed to this position. The notification will be sent to his/her email address in addition to the notification within the system. The corresponding record will also be saved in the history of changes to the position and company account.
Control of information transfer. Employees' access to information is based on the principle: ”everything created by me or provided to me is available”. The system prevents uncontrolled dissemination of information.
Each employee action generates an event. The event model helps to eliminate errors and increases trust in the information. All changes in the Company Settings section are logged in the system.
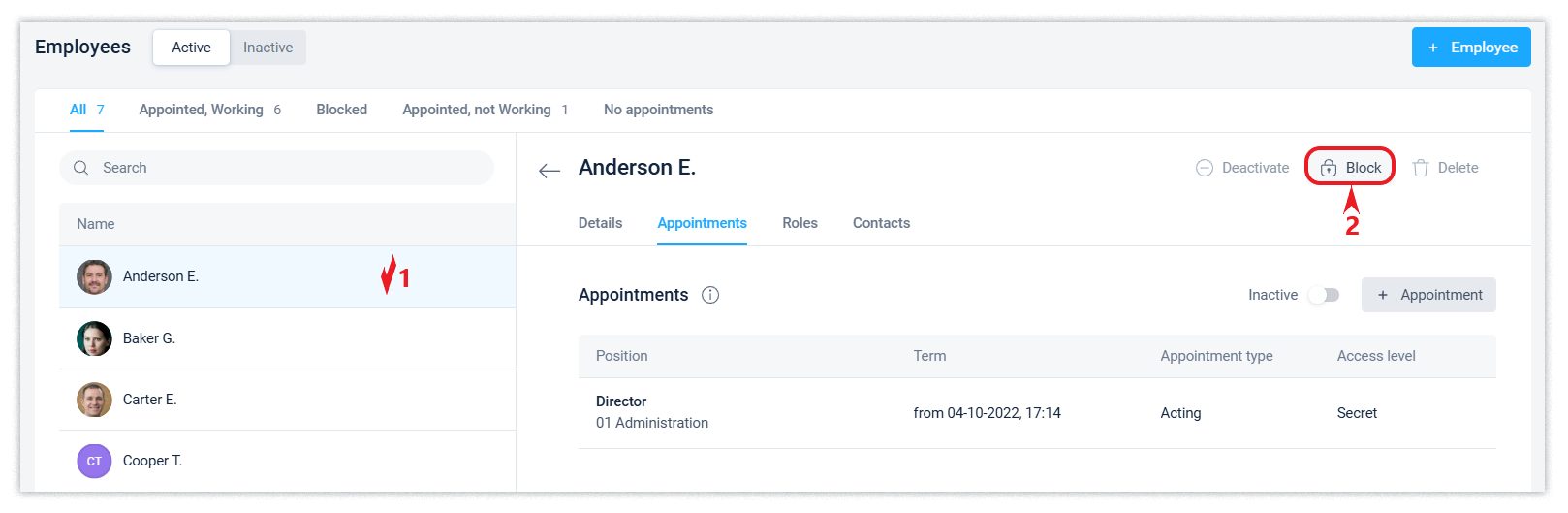
Quick access blocking. If there is a risk of unauthorized access to data, a user with the appropriate rights (administrator or owner) can block access for an individual employee.
GDPR (General Data Protection Regulation) compliance
We comply with the requirements of the EU General Data Protection Regulation (GDPR) and have implemented a wide range of technical and organizational practices.
