System principle: a user (employee) has access only to the information that he or she has created and to the information that other employees have given him or her access to.
The system is based on an event model - every user action generates an event. The author of the event, when creating it, as well as any employee who already has access to the event, can share it with other users. This approach ensures transparency of information dissemination and its integrity.
Granting access to system objects can be done in any of the following ways: sending for approval or signature, entering a notification to the recipients, opening access by a direct action, adding a file to the access when creating an event, creating a note, etc.
Granting access to an event or file also grants access to the system object to which the event or file belongs.
For more information about the basic elements of the system and the concepts of User, Employee, Position, Appointment, and Company, see the article Company Administration.
Access to system objects (document, task, etc.)
The author determines who will have access to the object and whether to grant access to edit it, in particular, he or she can leave access only to himself or herself. Later, any employee or external contact who has access to the object can grant access to it to other employees and contacts.
A position that, according to the company's communication rules, has the right to set tasks for the position of the object owner has the same right to change the object, including changing the right to edit it for themselves and other entities, as the object owner.
Access to a document means access to its basic data: subject, description, signatures and approvals, distribution and resolution, registration, and signature files.
Read more about access to documents in the relevant article.
Employees who have the right to read the log will automatically be granted access to those documents and valuables that are registered in this register.
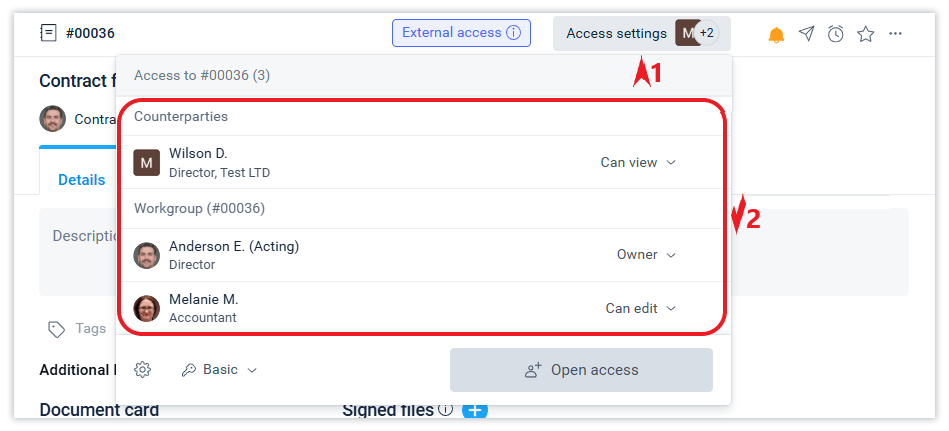
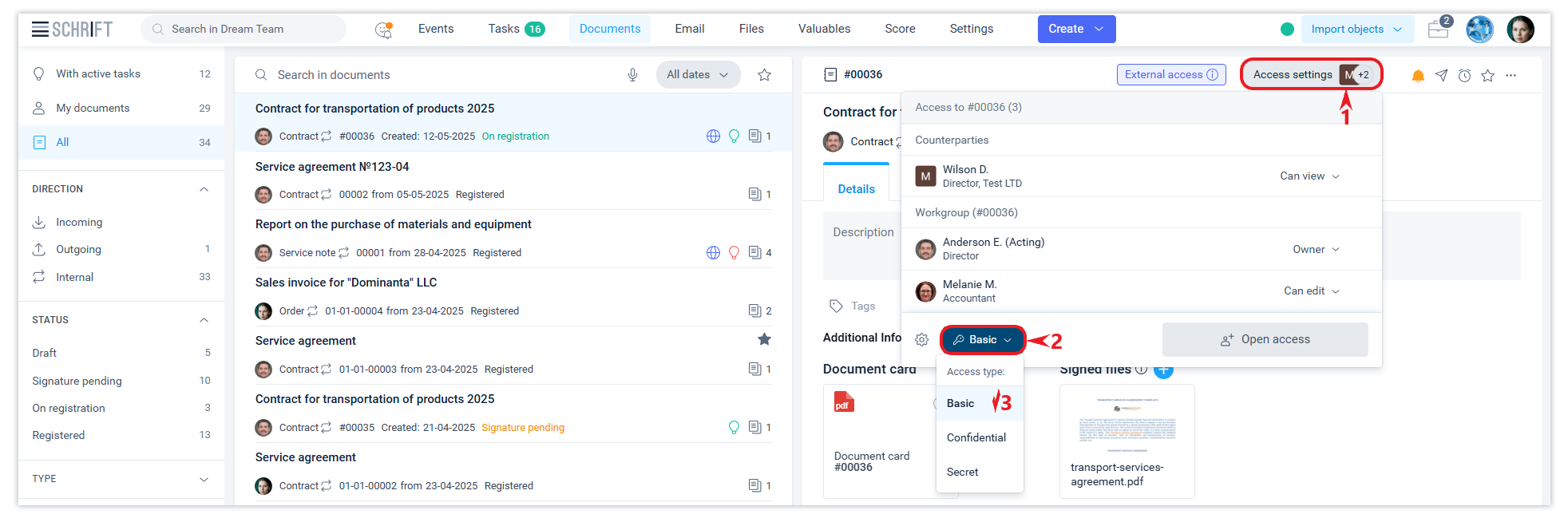
You can check who has access to the object and what kind of access they have in the Access settings form.
The author of an object can modify or delete it without any time limit if it is available only to him or her. If other employees have access to the object, then deletion will be available within the time period specified in the company's account settings. Read more about this in the corresponding article.
Access control
If you have the appropriate rights, you can control access. For example, you can change the read access to an employee or external contact to edit access or vice versa. You can also deny access to someone or yourself (leave the workgroup). You can manage access for a specific person in the Access settings form.
You cannot deny access to a document to a position in your company if that position has active tasks for that document or has access to the document by virtue of the right to read the log in which the document is registered. Read this article about closing access to external contacts.
The management capabilities depend on the user's role and the rights of the person for whom these access changes are to be made.
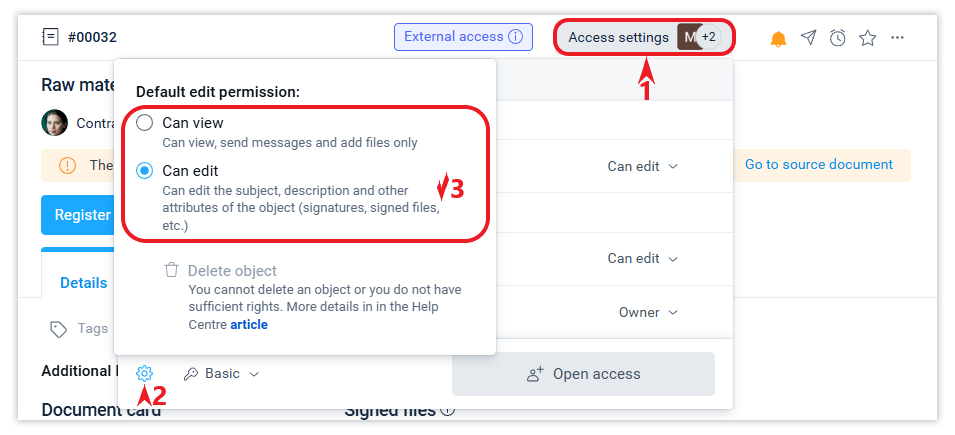
The so-called “administrative” rights to manage system objects also make it possible to delete an object by an action directly from the Access Settings form.
You cannot restrict access to a person who has an owner role. There are also restrictions on access control for external contacts of Schrift Intercompany, which you can read about in this article.
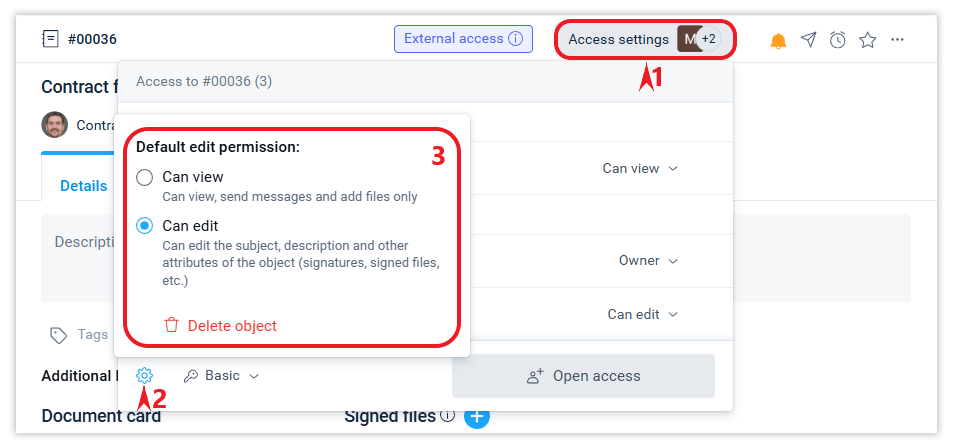
The default right to edit an object
In the general settings of the company, you can define whether the default editing permission for an object is read or edit for employees and external contacts.
In addition, the document owner can change the default object editing rights settings for new access participants in the properties of the object itself: when creating it - in the modal creation form or later in the Access settings form (see the screen).
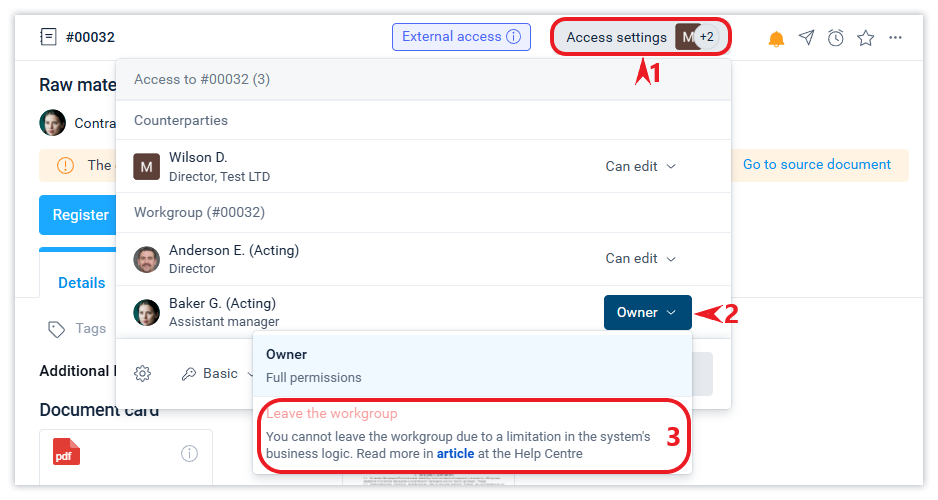
Closing access to yourself (leaving the workgroup)
You can deny yourself access to a system object by performing the Exit workgroup action in the Access settings form. This action may be relevant when the user does not need the object as part of the data available to him for various reasons, but he does not have the right to delete it.
You cannot deny yourself access to a document if access to it exists under the right to read the log in which it is registered. Open tasks on a system object also do not allow you to leave its workgroup.
Access to events
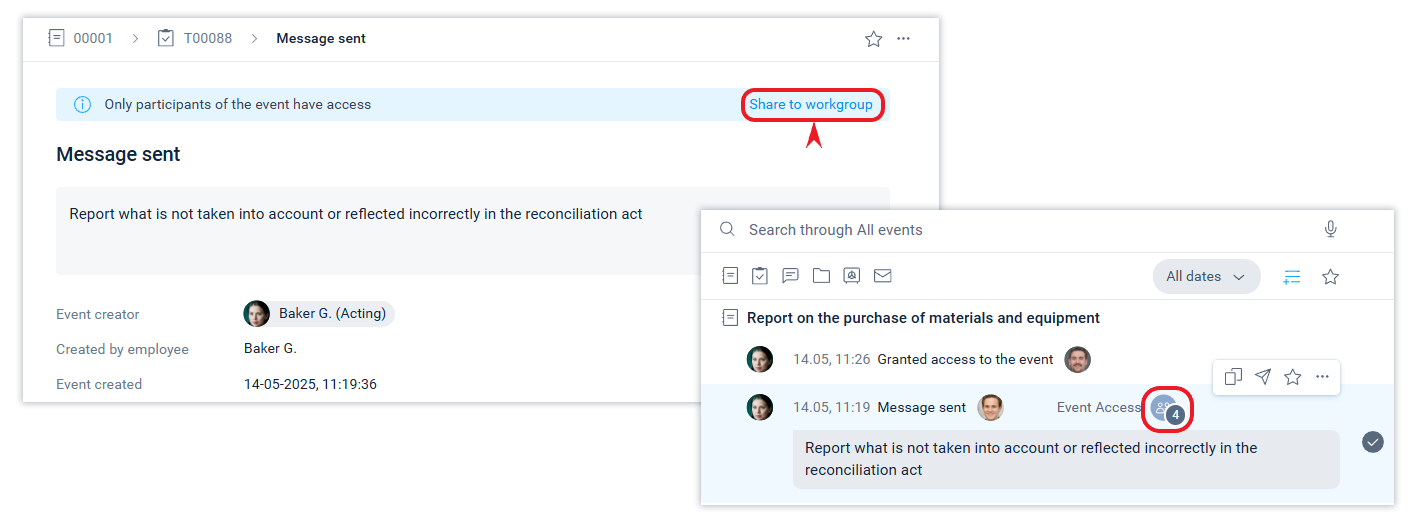
Any employee who has access to an event can share it with those who do not yet have access to it. The system supports the possibility of separate access to events within the framework of employee communication on one system object.
Granting access to any event in a document to an employee or external contact who does not yet have access to the document opens access not only to this event, but also to the document itself.
If an employee wants to receive notifications for all events available to them as a member of a workgroup, they just need to enable event tracking. In this case, the system will force notifications about such events to be activated for him.
You can close access to an event for an employee or an external contact from the Event details window.
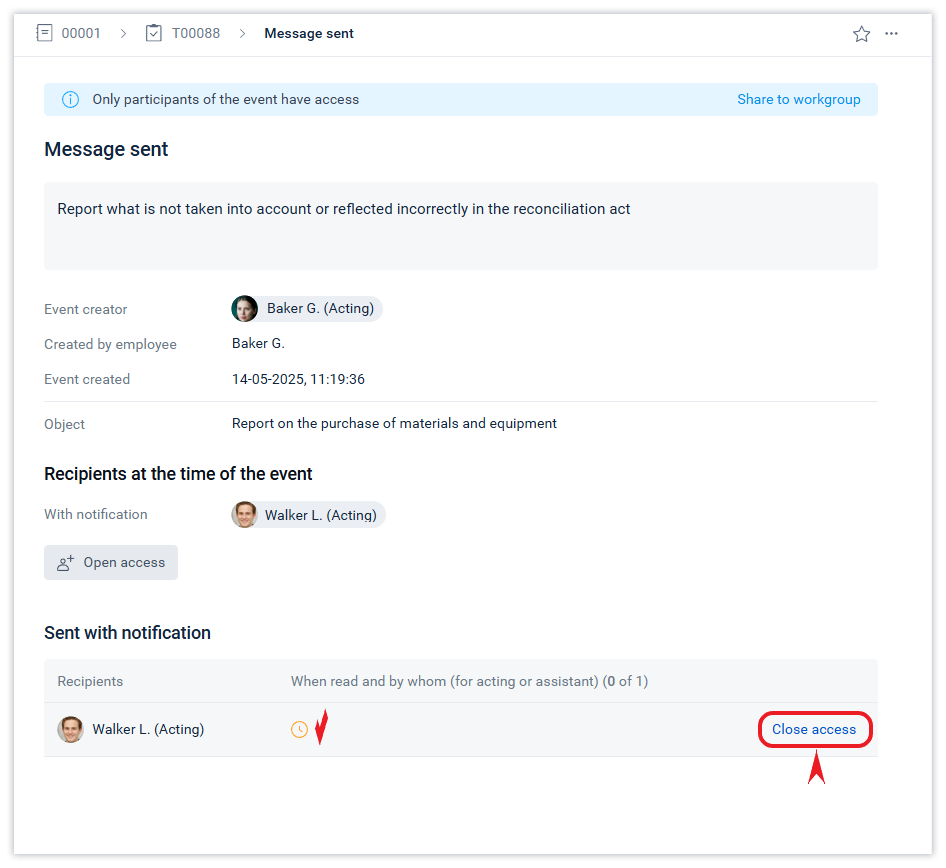
Only the author of an event can close access to it. The action of closing access to an event is subject to the restriction on deleting and modifying events described in this article.
But this restriction does not apply to the action of closing access for external contacts.
Closing access to an event will close access not only to this event, but also to the object (document, etc.) if this event was the only one available for the object. You can check whether access to the object is still available by using the list in the Access settings form.
None of the members of the workgroup can know exactly which events are available to other members of the workgroup, since they see only those events that are available to them. Therefore, closing access to all events does not guarantee closing access to the object. Read more about separate access to events in the article.
Working group
All company employees who have access to an object are members of its Working Group.
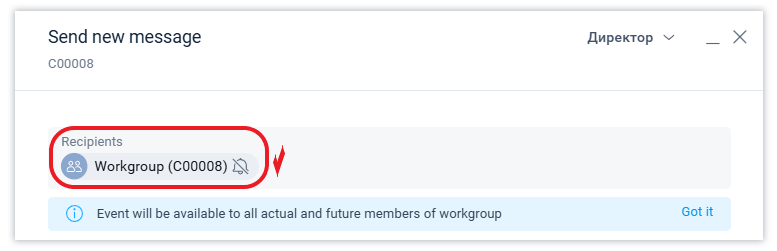
When creating any event, its author can set access to it for members of the workgroup, which means that all current and future members of the workgroup will have access to this event. That is, the access set to a workgroup also works as an event property. Read more about this in the corresponding article.
Accessing files
Files are always part of a system object. Adding files also triggers an event, so access to the event is also access to the file. Thus, everyone who has access to the file add event has access to the file.
You can check access to a file in the Files tab and when viewing a file.
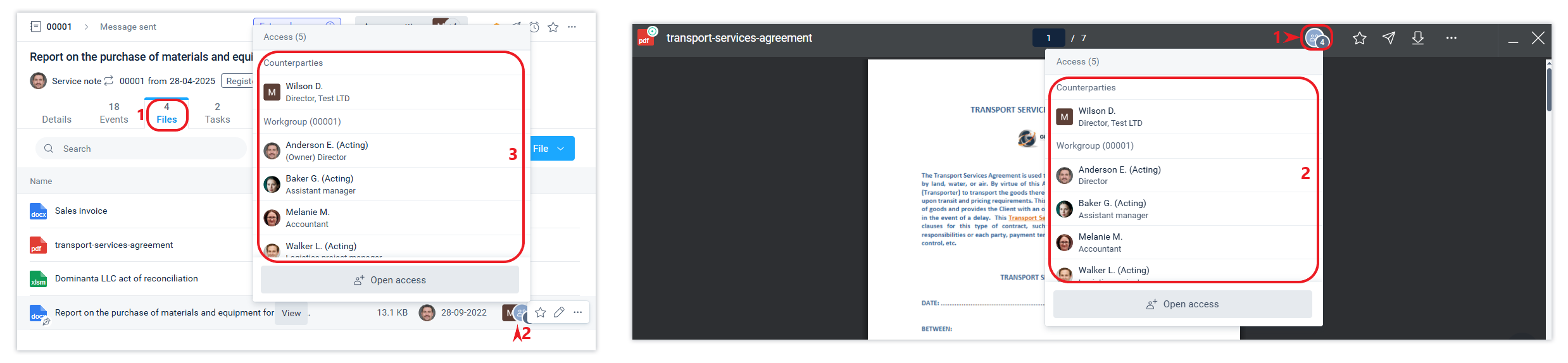
The files of the document to be signed are always available to the members of the working group of that document.
Access levels for objects and assignments
There are 3 access levels in the system: Basic, Confidential, and Secret. A system object is assigned the Basic access level (the lowest level) by default. Any member of the workgroup can change the access level of the object within the levels available to him.
Appointing an employee to a position also sets their access level. The access level of the appointment determines what level of confidentiality of objects the employee assigned to this position can access.
An employee appointed to a position on a regular basis may appoint another employee Acting/Reference with an access level not higher than his/her own.
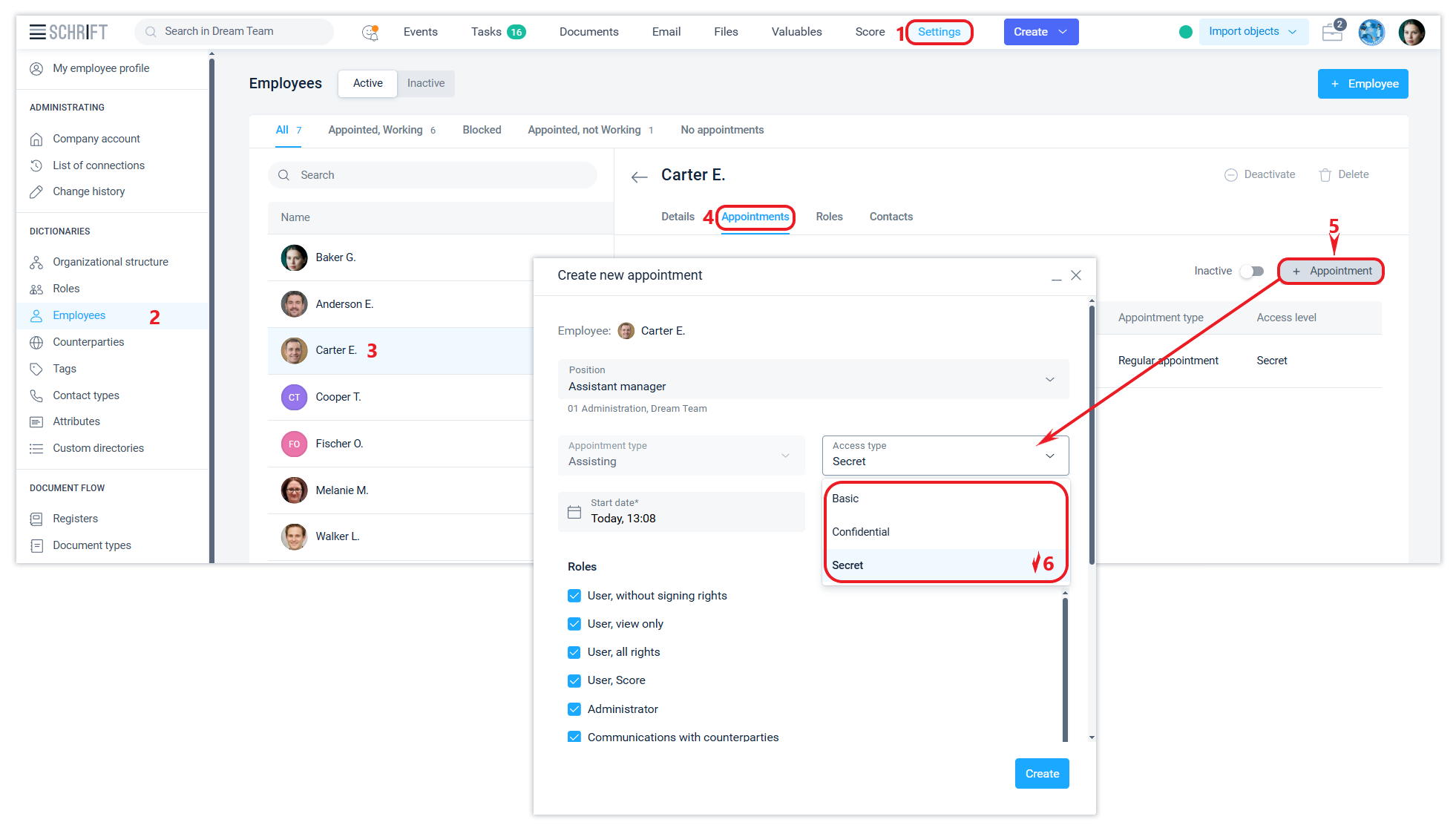
An employee who has an appointment with the Confidential access level will not see objects with the Secret access level, and will not be able to set an access level for a system object higher than the access level of his appointment.
Managing the level of access to system objects and assignments makes some sense when assigning acting or reference persons who are assigned a lower level of access in the assignment than the staff member, which allows you to leave some information available only to the staff member.
If an employee with Secret access level changes the access level for a document from Basic to Secret, another employee with Confidential access, who previously had access to this document, will lose access to the document after this action.
